Crossing paths in Las Vegas and announcing a new open source project

We had a great time in Las Vegas meeting and interacting with the community. Several of our Datadogs presented at BlackHat, DEF CON, and BSides Las Vegas. Here are a few highlights:
-
Nick Frichette presented his research on exploiting cloud providers' very own vulnerabilities to break into cloud environments.
-
Zander Mackie demonstrated an unexpected way to backdoor Azure environments using Azure Policy, a service commonly used by blue teamers.
-
Seth Art delivered his workshop on exploiting common vulnerabilities in AWS environments.
-
Christophe Tafani-Dereeper presented attack vectors when using OIDC authentication in AWS, and a practical approach to detection engineering and purple teaming in cloud environments.
On the open source side, we released Grimoire, a new open source project to help with the detection engineering process in cloud environments. It helps you generate datasets of CloudTrail logs for common attacks. We also had the opportunity to demonstrate several of our open source tools at BlackHat Arsenal, including Stratus Red Team, KubeHound, and the Managed Kubernetes Auditing Toolkit.
If you want to read more, head over to our hacker summer camp 2024 write-up!
Kubernetes authorization in practice
Ever wondered how authorization worked in Kubernetes environments? In the latest post in our "Kubernetes security fundamentals" series, Rory McCune dives into concepts such as role-based access control (RBAC), webhook authorization, and the Node Authorizer.
READ THE POST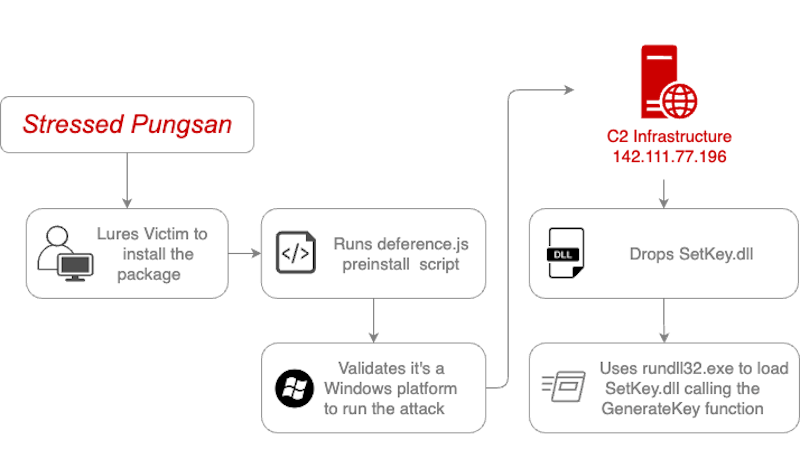
Nation-state threat actor deploying malicious npm packages
The Datadog security research team identified a malicious npm package targeting Windows machines. After infecting the victim, it downloads a Dynamic Link Library (DLL) from a remote server and executes it. We have attributed this attack to an attacker group aligned to the North Korean government.
READ THE ANALYSIS
GuardDog v2.0 is out!
We have recently released GuardDog v2.0, which includes support for custom rules, support for YARA rules, improved detections, and initial support to scan Golang packages.
SEE THE NEW FEATURES
TrailDiscover
TrailDiscover is an helpful community project by Adan Álvarez that lists common CloudTrail events and cross-references associated attacks in the wild.
TRAILDISCOVER.CLOUD
Log4Shell exploitation identified in the wild
Through a network of honeypots, our security research team identified active exploitation of the Log4Shell vulnerability in the wild. This post describes the exploitation activity and provides an in-depth analysis of the malicious payloads.
READ THE ANALYSIS
fwd:cloudsec Europe 2024 is around the corner
fwd:cloudsec is the first vendor-neutral conference for cloud security practitioners. The first Europe-based edition is coming to Brussels on September 17th! All the talks will be streamed online for free. As a gold sponsor, we're proud to support this inaugural edition.
VIEW THE FWD:CLOUDSEC EUROPE SCHEDULEDatadog Security Releases
Agentless scanning: Detect vulnerabilities in minutes with Cloud Security Management

We're excited to announce the general availability of Agentless Vulnerability Scanning for Cloud Security Management (CSM), starting with AWS. You can now uncover and remediate prioritized vulnerabilities across your entire infrastructure in minutes, without having to deploy the Datadog Agent on every host.

Agentless scanning works locally to your cloud account, so potentially sensitive data never leaves your environment. It supports virtual machines, containers, and serverless functions on AWS. Support for Azure and Google Cloud will be available in Q4 2024.
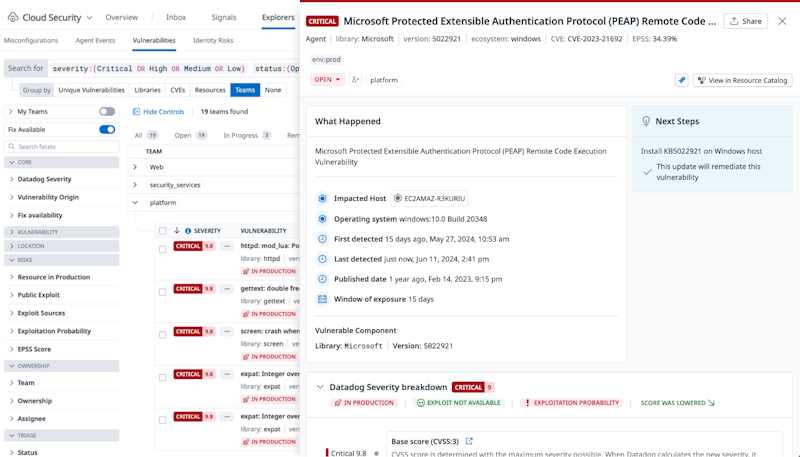
Cloud Security Vulnerability Management for Windows hosts
You can now identify vulnerabilities on Windows-based systems using CSM Vulnerability Management, as well as prioritize and visualize them from a single central location with customizable out-of-the-box dashboards.
LEARN MORE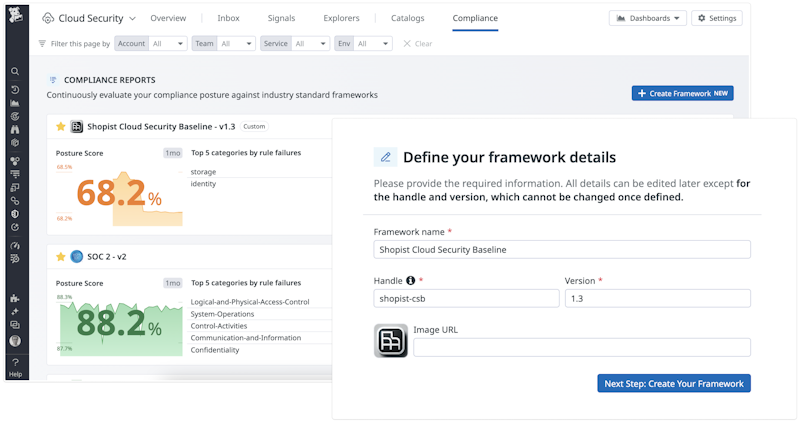
Define custom compliance frameworks in Cloud Security Management
You can now craft cloud security baselines tailored to your own needs to simplify cloud security governance across your organization. Pick from 1,000+ default rules or create your own.
READ THE DOCS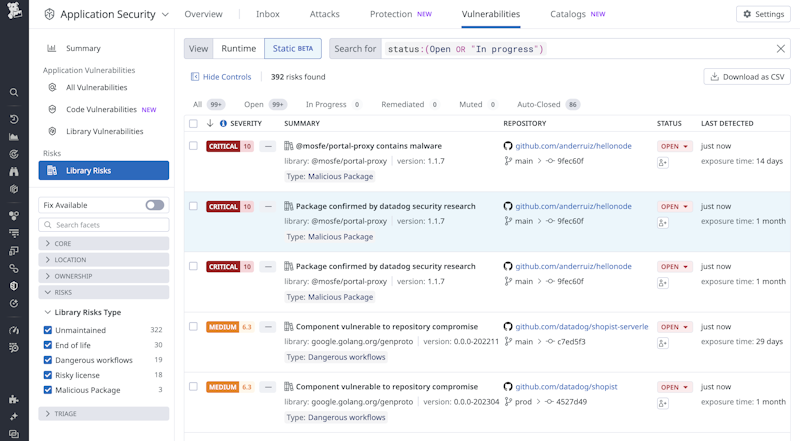
Identify problematic open source dependencies with Datadog SCA
Datadog Software Composition Analysis (SCA) now allows you to identify problematic open source dependencies such as licensing risks, end-of-life libraries, unmaintained projects, and actively malicious dependencies.
VIEW RELEASE NOTES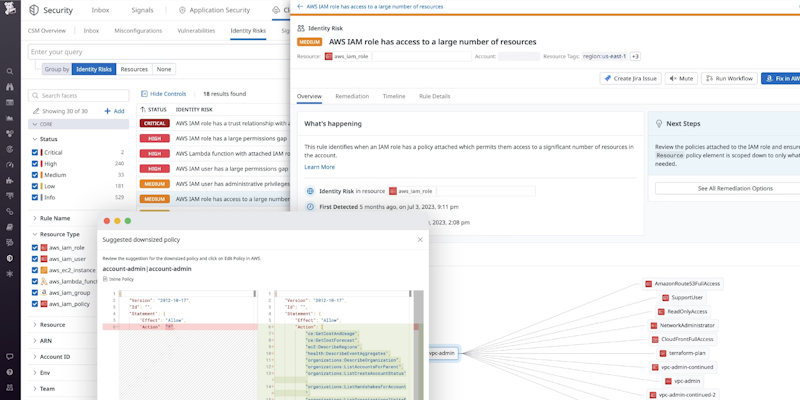
Datadog °CIEM now supports all three major cloud providers
Datadog Cloud Infrastructure Entitlement Management (CIEM) now supports AWS, Azure, and Google Cloud. CIEM helps you identify identity risks in your cloud environments, including visualizing permissions and trimming down privileges based on cloud audit logs.
READ THE DOCS