The State of Cloud Security in 2024, Google Cloud default service accounts, and attackers using Docker Swarm

Our latest research report, the State of Cloud Security 2024, is hot off the press! In this study, we analyzed security posture data from thousands of organizations using AWS, Azure, or Google Cloud. Key insights from the report include:
- Long-lived cloud credentials remain a significant risk, with 46 percent of organizations using IAM users to authenticate to the AWS console.
- Less than half of EC2 instances enforce IMDSv2, though adoption has been rapidly increasing since 2022.
- The adoption of S3 Public Access Block is also on the rise, now covering four out of five S3 buckets.
- Many cloud workloads are overprivileged across both AWS and Google Cloud, which can lead to excessive data access, lateral movement, or privilege escalation.
Additionally, we examined the security posture of managed Kubernetes clusters, IAM roles utilized for third-party access by known SaaS vendors, and insights from various cloud incidents we’ve observed.

Challenges with IP spoofing in cloud environments
While accessing an end user's IP address may seem trivial, it can get complex in cloud environments, which often have one or more layers of reverse proxies or load balancers. In this post, one of Datadog's security researchers explores some of these challenges and provides exclusive insights by looking at HTTP requests in the wild from thousands of organizations.
Read the post
Remote code execution exploit chain in CUPS
A new attack leveraging a series of vulnerabilities in the printing software CUPS was disclosed on September 26. Successful exploitation requires chaining together four distinct vulnerabilities and tricking a user on the target machine into initiating a print job. While this discovery may significantly impact desktop environments, it’s unlikely to be exploitable in cloud environments. However, it’s always wise to minimize the internet exposure of your virtual machines.
Read our analysis of the vulnerability
Attackers exploiting Docker Swarm and Kubernetes to mine cryptocurrency
Datadog researchers recently uncovered a campaign targeting open Docker Engine APIs. While attacks on these APIs are not unusual, some tactics here stand out. For instance, attackers are joining compromised hosts to a malicious Docker Swarm cluster, allowing them to control these systems remotely with ease.
Read the analysis
Malicious use of GenAI models in compromised cloud environments
Since early 2024, several security companies, including Datadog, have observed attackers reselling access to hosted GenAI models within compromised cloud environments. In a detailed analysis, Ian Ahl sheds light on this trend, offering exclusive insights into an underground economy that leverages proxied access to LLMs. Thanks to a contribution from Alessandro Brucato, Stratus Red Team now supports emulation capabilities for this specific attacker behavior.
Read the post
Mandatory MFA is coming to Microsoft Entra ID
Mandatory MFA for Microsoft Entra ID has arrived. As of October 15, 2024, Microsoft enforced MFA for high-value targets, including the Azure portal and the Microsoft Entra admin center. If you’re using Entra ID or Azure, ensure your administrators have MFA enabled—ideally through a phishing-resistant method like FIDO2.
Read the roll-out planSecurity Event Spotlight

Datadog On: Cloud Workload Identities
In this Datadog On episode airing November 5, two of our staff engineers will showcase a novel approach for enabling secure, efficient resource access across AWS, Azure, and Google Cloud—all without requiring configuration changes to applications. They’ll discuss how they developed a zero-configuration sidecar container that emulates cloud provider instance metadata APIs, allowing seamless access to cloud resources within a Kubernetes environment.
Register
The video recordings for fwd:cloudsec Europe are out!
fwd:cloudsec Europe happened in Brussels on September 17. Several of our researchers and engineers were present, and we were proud to support this inaugural event as a Gold sponsor. All the talk recordings are now freely available on YouTube!
Watch the talksDatadog Security Releases

Track operational security metrics with Cloud SIEM. Datadog Cloud SIEM now enables you to track critical security operations metrics, such as time-to-detect (TTD), time-to-acknowledge (TTA), and time-to-resolve (TTR). These metrics are automatically included in weekly digest reports and are available on out-of-the-box dashboards for easy monitoring.

Key learnings from the State of Cloud Security study
Building up on our latest State of Cloud Security research, this post extracts some key learnings and showcases how to use Datadog Cloud Security Management (CSM) to solve some of these all-too-common misconfigurations in cloud environments.
Read the post
New CSM Misconfiguration rules and attack paths
Several new detection rules have been introduced within Datadog CSM for misconfigurations and attack paths. Alongside 28 new rules based on AWS Foundational Best Practices, we've added capabilities to detect publicly accessible Amazon ECR repositories, Amazon RDS instances with easily guessable usernames that are publicly accessible, and publicly accessible EC2 instances vulnerable to the recently identified CUPS vulnerabilities.
See detection rules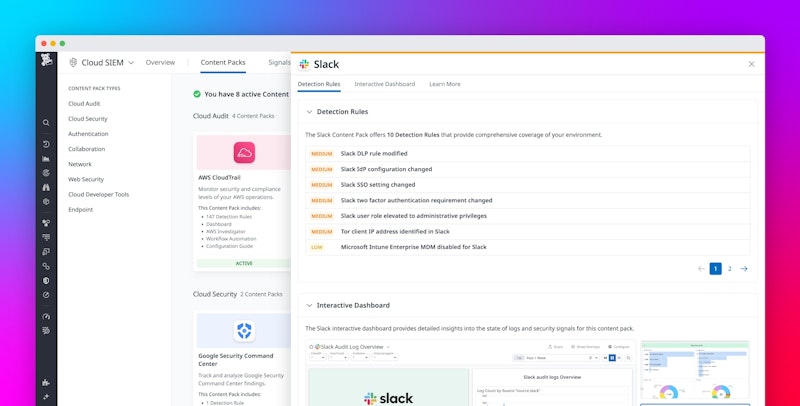
Monitor your Slack audit logs
Slack's tagline, "where work happens," also makes it an attractive target for attackers. The new Slack content pack offers out-of-the-box dashboards and detection rules to help identify potentially malicious activity, such as data exports from a workspace or disabling multi-factor authentication (MFA) requirements.
Read the announcement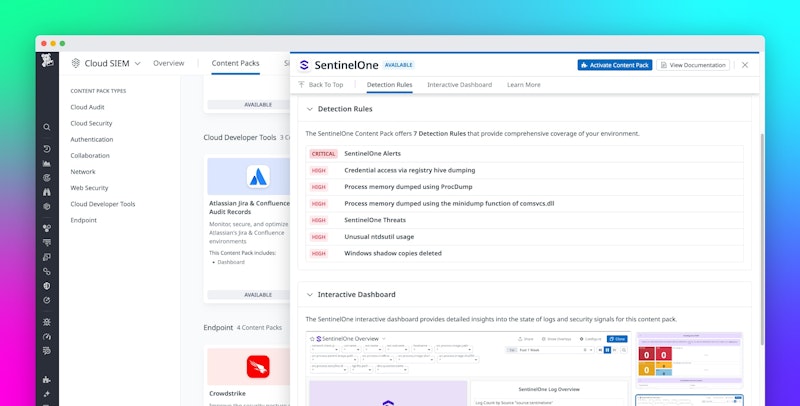
Monitor your SentinelOne logs and alerts
SentinelOne is a popular endpoint detection and response (EDR) solution. With the new content pack, you can access centralized alerts, threats, and telemetry within Datadog. Once the data is integrated, you can leverage advanced Cloud SIEM features, such as Signal Correlation, to build sophisticated detections. For instance, you could identify a compromised developer laptop followed by suspicious activity from that developer within a cloud environment.
Read the announcement