Securely integrating with customers' AWS accounts, supply chain security, and investigating a DoS attack

We've recently released a guide for SaaS providers to securely integrate with customers' AWS accounts. It goes through not only the basics, but also hardening and architectural tips, including:
- Leveraging short-lived credentials
- Protecting against "confused deputy" attacks by asking customers to enforce external IDs and actively making sure these are properly controlled
- Providing configurable infrastructure-as-code modules
- Building a UX that allows your customers to selectively enable product features to achieve minimally privileged integration roles
- Using STS session policies in a distributed backend architecture to limit the permissions of each sub-integration
This guide is certainly relevant if you work on a SaaS application with AWS integrations. It's also relevant if you're using or evaluating such vendors, so you can challenge them and assess their security posture based on the permissions they require and the type of data they're processing.

Kubernetes security fundamentals: Admission control
Kubernetes clusters are only as secure as what they run. Admission control is a common way to gain control and visibility over the runtime configuration of your workloads. This post dives into how admission control works and how you can use it in practice.
Pssst—did you know that attackers can use admission controllers to backdoor a compromised cluster?

Hijacking abandoned PyPI packages
JFrog researchers discovered that over 20,000 previously deleted PyPI packages are still being installed by applications that have not updated their dependencies. This vulnerability would allow an attacker to register packages with the same name and compromise any application or machine that installs it. By hijacking one of these vulnerable packages using non-malicious code, researchers obtained 180,000 install requests.
Read the post
Malicious software package dataset
Speaking of malicious packages—have you ever analyzed one? We have a public dataset of over 1,600 human-triaged malicious PyPI and npm packages to play with, which we update on a weekly basis. A few months after we released it, the OpenSSF also released a GitHub repository with their samples.
Show me supply chain malware
Typos in GitHub actions names considered harmful
Typosquatting popular artifacts to trick developers into installing malicious software is not new. But researchers recently used this technique to create GitHub Actions with names such as actons/checkout instead of actions/checkout and watched the suspense unfold. Spoiler: It worked. Bad news: There's no straightforward way to prevent making mistakes in package names. Want to see GuardDog support for scanning GitHub Actions? Vote here.
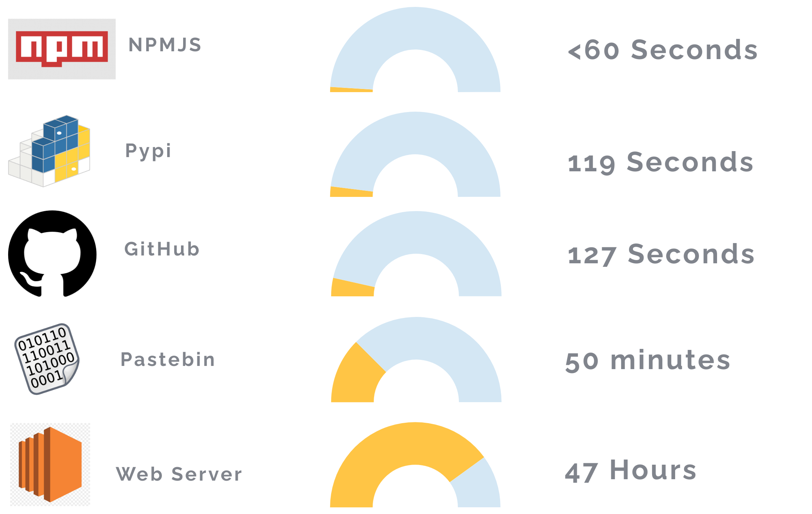
Alright then, keep your AWS secrets
Ever wanted to drop credentials all over the place, then watch the world burn while sipping a fresh drink? That's what Idan did (minus the drink), and the results are interesting. It took less than three minutes for his access keys dropped on PyPI, npm, and GitHub to be compromised, and just over two days for the ones exposed through a web server. Meanwhile, nobody looked at GitLab or Bitbucket. A good reminder that the best way to not leak long-lived access keys is to not have long-lived access keys in the first place.
Read the post
fwd:cloudsec Europe is a wrap!
fwd:cloudsec Europe happened in Brussels on September 17. Several of our researchers and engineers were present. Don't miss Nick Frichette's talk on undocumented AWS APIs and Katie Knowles' presentation on abusing Entra ID administrative for sticky tenant persistence. You'll also want to see Rami McCarthy's "How to 10x Your Cloud Security Without the Series D."
Read the recap and slides
Stratus Red Team now supports Entra ID attack techniques
Stratus Red Team is an open source project that allows you to easily simulate common cloud attacks. We're excited to announce that it now supports Entra ID and ships with five real-world attack techniques to detonate in Entra ID environments.
See the new Entra ID attack techniques
A deep dive into how Datadog mitigated a complex DoS attack
A few months ago, Datadog was targeted by a DoS attack. This is a great writeup from engineers who responded to and mitigated the incident. Hint: It involves L4 load balancers, Envoy, and HTTP smuggling.
Read the write-up
A CISO and a Director of Security Research walk into a stream
Interested to learn more about securing cloud environments? Join us for a special live event on October 16 where we’ll discuss strategies for securely building in the cloud. Ami Dave (CISO at Fanatics) and Zack Allen (our very own Senior Director of Security Research) will be joining us.
Register
The recordings for BSides Las Vegas are out
BSides Las Vegas began in 2009 as the first conference of what's now a decentralized network of events around the world. If you weren't in Las Vegas back in August of this year (which is, statistically speaking, extremely likely), the recordings are now available for free on YouTube!
See the talksDatadog Security Releases
How the Datadog Security Inbox prioritizes security risks

Less is more. In cloud environments, cutting through the noise and focusing on what matters most is essential. Read about the methodology we use to prioritize security risks, how we leverage observability data, the exploit prediction scoring system (EPSS), and unified severity scoring. We also correlate posture data across the stack, from the application to the cloud and through the container.
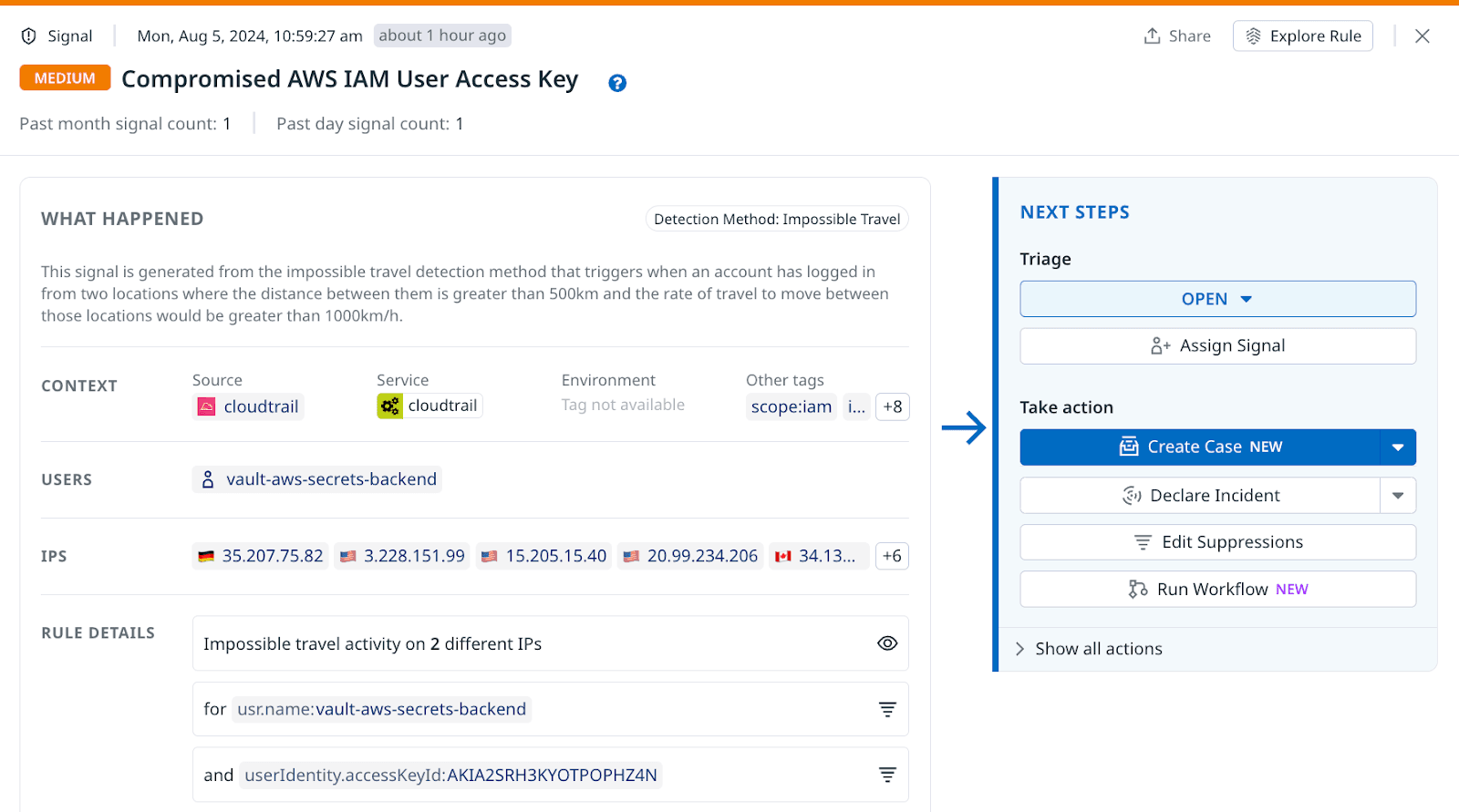
Shorten investigations with a new Cloud SIEM side panel
Investigating SIEM signals can be daunting when you have to switch back and forth between different data sources and views. We've redesigned the detailed Cloud SIEM signal view to do the hard work of simplification and make sure you have everything at hand while minimizing noise.
Read more about investigating security signals
New CIEM detections for cross-account lateral movement in AWS
Datadog Cloud Infrastructure Entitlement Management (CIEM) now detects cross-account lateral movement—namely, when one of your EC2 instances, IAM user, or IAM role has effective permissions to assume an administrative role in another account that's part of your AWS organization. When it finds one, it will show it nicely in a graph so you can understand what's happening in seconds.
See the rules in-app
Proactively classify and redact sensitive data in Datadog
When sending high volumes of observability data, excessive or unintended logging can sometimes lead to sensitive data exposure. Datadog Sensitive Data Scanner (SDS) allows you to scan Logs, APM spans, RUM events, and Events to classify and redact sensitive data. You can also watch Block's talk at DASH 2024 about systematically filtering PII from logs at different layers.
Read the post