Q2 threat report, prompt injection, and fwd:cloudsec Europe

Welcome to the August 2025 edition of the Datadog Security Digest!
This edition covers Datadog's Q2 threat report, new cloud security research, AI security vulnerabilities, application security findings, and upcoming community events. We hope you enjoy catching up on the latest in cloud security!
This newsletter was created by a real person, not a machine. Your curators of the month are Kennedy Toomey and Christophe Tafani-Dereeper.
Datadog's Q2 threat report
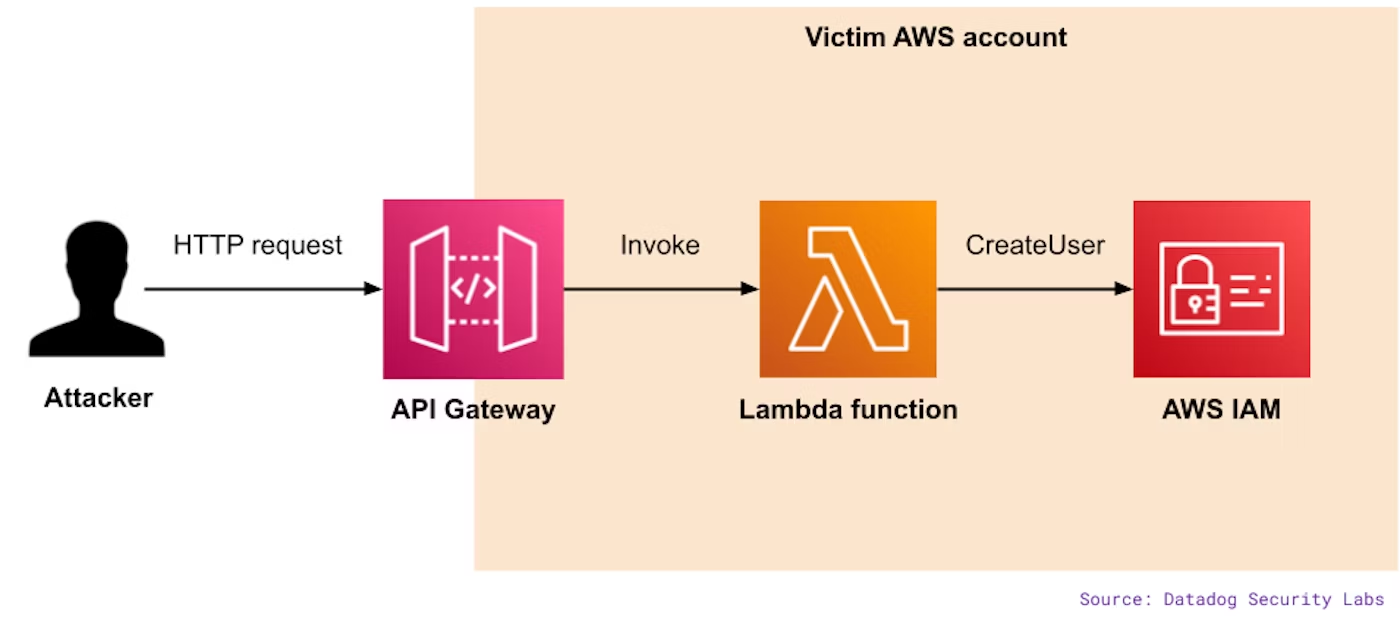
Read Datadog's update on the most common threats we've witnessed in Q2. From supply-chain attacks to a novel cloud persistence technique and a threat actor targeting the Magento CMS, our security research team shares their technical insights. One interesting finding is an attacker who's been persisting in victims' AWS accounts by creating an API gateway and Lambda function that they can later use as a backdoor by sending HTTP requests.
Cloud security
Threat detection in the cloud versus on-prem
Migrating data and workloads to cloud environments also means detecting threats in the cloud. This provides both some great opportunities (for instance, APIs), but also challenges and paradigm shifts. Chester Le Bron goes in-depth on how cloud investigations vary from the on-premise world, and how to make the most of it.
Blocking Amazon EKS pod access to the IMDS
One of the most important steps to secure an EKS cluster is preventing pods from reaching the instance metadata service (IMDS). Otherwise, a compromised application could let an attacker pivot and escalate their privileges, as we demonstrated in our 2023 KubeCon talk and related blog post. Terry Franklin shares some more wisdom and dives deeper on some possible ways to block or secure pod access to the IMDS.
CloudTrail-free discovery with Resource Explorer (remediated)
Our own Nick Frichette details an unexpected behavior from AWS Resource Explorer, which would have allowed an attacker to enumerate all resources in an AWS account using resource-explorer-2:ListResources, without logging to CloudTrail by default, because the event was classified as a CloudTrail data event.
AI security
Critical vulnerability in Claude Code extension
Anthropic patched a vulnerability in a Claude Code extension that would have allowed any malicious website to execute arbitrary code on a vulnerable machine, due to a WebSocket server that did not enforce authentication. Datadog's Zander Mackie showcases a PoC for the vulnerability, along with an analysis of the official patch.
The lethal trifecta in securing MCP
Simon Willison describes his idea of the lethal trifecta that is created when using MCP servers: access to private data, ability to externally communicate, and exposure to untrusted content. Willison claims that removing any one of those vectors is sufficient to prevent attacks.
Hands-on prompt injection to exploit GitHub Copilot
The Trail of Bits team shared a very detailed demonstration of a real-world prompt injection attack on GitHub Copilot. It's slightly more complex than writing "ignore previous instructions" in a chatbot interface, which makes it much more realistic and relevant to anyone eager to learn the practical applications of prompt injection attacks.
Application security
The impending death of HTTP/1.1
This month at Black Hat USA and DEF CON 33, James Kettle shared new HTTP desync attack variants capable of large-scale credential compromise. In the accompanying blog post, he shares real-world findings from six years of research that has resulted in over $350,000 in bounties earned. As a result of this research, HTTP/1.1 Must Die was created to encourage its demise.
Proactively identifying GitHub Actions workflow injections
In a GitHub Actions workflow injection, an attacker can inject a command that the repository’s workflow then executes. Fortunately, these vulnerabilities are easy to detect and fix by applying common coding best practices and restricting the use of pull_request_target.
Community events and talks
fwd:cloudsec Europe is around the corner
Taking place in Berlin on September 15-16, fwd:cloudsec Europe is the second European edition of the fwd:cloudsec conference, an advanced practitioner-focused conference about cloud security. There are a number of exciting talks there, including "Mastering AWS Honey Tokens to Detect and Outsmart Attackers" by our own Nick Frichette. Note that the talks will be livestreamed online for free.

