At DASH 2025, we released a Datadog expansion pack of Backdoors & Breaches, a popular incident response card game by Black Hills Information Security. We gave away a copy of the core deck and the Datadog expansion pack to everyone who visited the Datadog Security Zone at DASH, and we had live games for attendees to join. Our expansion pack is also available in an online format so that distributed teams can use it to play.

What is Backdoors & Breaches?
Designed to be both educational and engaging, Backdoors & Breaches helps teams sharpen their cybersecurity and incident response skills through simulated attack scenarios. Players respond to a given scenario to uncover attack pathways that were used to breach an environment.
Six types of cards make up a deck:
- Attack cards, which include the following four types:
- Initial Compromise: How did the attackers gain access?
- Pivot and Escalate: How did the attackers gain privileges after they gained access?
- Persistence: How do the attackers maintain access?
- C2 and Exfil: How do the attackers communicate with the service from outside?
- Procedure cards: Ways to detect an attack
- Inject cards: Scenario twists that simulate random events that occur during security incidents
The game is ideal for tabletop exercises, team collaboration, and students who are learning how to respond to an incident. Whether you're a seasoned security professional or you’re new to incident response, Backdoors & Breaches offers a hands-on, collaborative way to practice your response playbooks in a safe, low-stakes environment.

Why use the Datadog expansion pack?
Datadog has many security and observability products that you can use for incident response. The Datadog expansion pack gives security and engineering teams the opportunity to prepare for real-world incidents by building muscle memory with the same observability and security tools that they rely on every day. With the expansion pack, teams can simulate incidents that reflect their actual monitoring and security setups to better tailor the tabletop exercises to their needs.
How to play
An Incident Captain facilitates the game, while the other players take on the role of Defenders. The Incident Captain secretly selects one card from each Attack category and keeps these four cards hidden. The Incident Captain creates and presents a realistic scenario that is based on the Attack cards, providing enough context to guide the game without revealing the specific attack methods in play.
The Defenders must work together by using critical thinking, Procedure cards, and a 20-sided die to investigate the scenario and uncover the hidden Attack cards. If they successfully identify all four Attack cards within 10 rounds, the Defenders win!
The full instructions are available in the Backdoors & Breaches Visual Guide.

Starter scenarios
You can create countless scenarios by using the Datadog expansion pack alongside the core Backdoors & Breaches deck. If you're looking for inspiration, here are a few example scenarios that we've used to spark engaging and realistic incident response exercises.
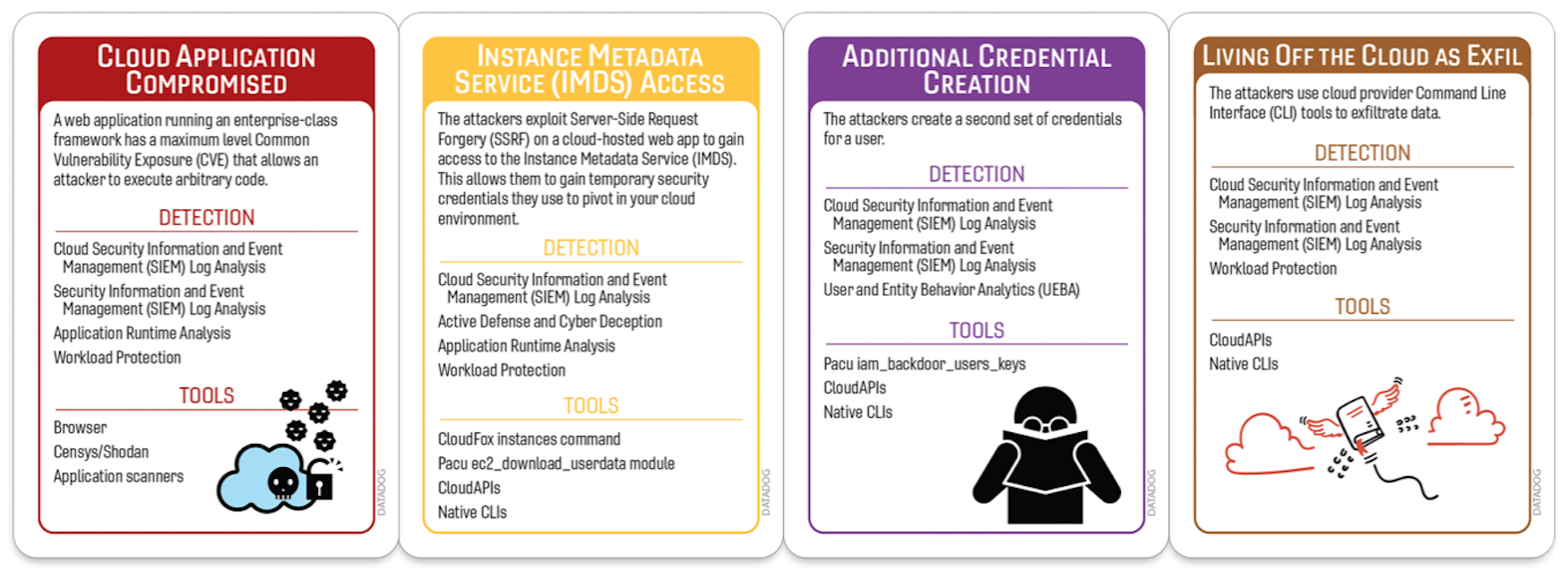
Scenario 1: Your cloud application was compromised
Background: Web application exploitations are still on the rise.
Scenario: Your DevOps team notices that your monolithic application has behaved suspiciously since the last deployment, which happened that morning. The team also mumbles something about an unusual number of Access Denied errors in AWS CloudTrail logs.
- Initial Compromise: Cloud Application Compromised
- Pivot and Escalate: IMDS Access
- Persistence: Additional Credential Creation
- C2 and Exfil: Living off the Cloud as Exfil
Scenario 2: Your SSO federated identity was compromised
Background: Phishing campaigns that target cloud administrators are easy to launch and cause harm when they succeed.
Scenario: Your cloud infrastructure monitoring system begins flagging unusual activity performed by a newly onboarded AWS administrator. After suspecting an insider job and investigating the employee's endpoint, you understand that they did not knowingly perform any malicious actions themselves.
- Initial Compromise: Compromised SSO Federated Identity
- Pivot and Escalate: Credential Store Compromise
- Persistence: Backdoored Role Trust Policy
- C2 and Exfil: Snapshotting Resources as Exfil
Scenario 3: Your CI/CD pipeline was compromised
Background: GitHub Actions are an increasingly popular option for continuous integration because they work natively with GitHub, a common choice for version control.
Scenario: Customers of your ecommerce application that is running on Amazon EC2 are reporting that the website was unavailable for several minutes. Your deployment logs show no recent code pushes or infrastructure changes. You receive an AWS Cost Management alert that informs you that your egress network bill has increased by 25 times today.
- Initial Compromise: GitHub Action Compromised
- Pivot and Escalate: Instance Takeover Via User Data
- Persistence: Backdoored Container Image
- C2 and Exfil: SaaS Tunneling VPN as C2

How to get started playing
Are you as excited about the Datadog expansion pack as we are? If you didn’t get a physical deck at DASH, you can pick one up at the Datadog booth at future security conferences or purchase one from the online store. If you want to play with a distributed team, you can also play online.





